I didn’t believe it at first when I read this article today. However, if you are that power-user kind of guy or gal who isn’t afraid of the command line, you can do the same experiment that I performed and discover the hidden backdoors in the very backyard of your Xiaomi phone or tablet. Here is what I did on my stock Xiaomi MiPad-1 tablet running the KitKat based MIUI (Global ROM v7.5.2.0) to discover these backdoors (you don’t need to be rooted in order to do this):
- Head over to the Play Store and install any terminal app, the one from Jack Palevich is the standard one.
- Disconnect from Internet and restart the device (Make sure that you greenify all apps that start automatically in background like WhatsApp/Skype before that).
- Now, without connecting to the Internet, open the terminal app and run this command to check for open tcp connections: netstat -atp
- It should show you zero connections as you are not online yet.
- Now, start the internet and after a few seconds, run that command again. What should you ideally see? Zero connections because you don’t have any app running yet. However, this is what I saw:
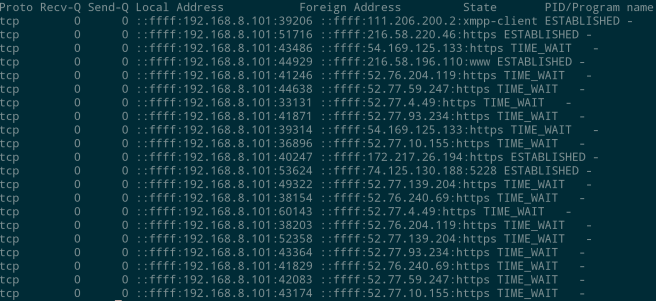
What this means is that Xiaomi has a background app constantly running which establishes a connection with some backend servers as soon as you connect to the Internet. For example, as shown on the first line, an app is listening on the XMPP port and connected to the IP 111.206.200.2. When I looked up this IP Address on the Internet, it was traced to some Chinese ISP, thus confirming my suspicion.
What this essentially means is that the person on the other end of this connection may be doing anything to our device through this established tcp connection. Now, it could well be the case that the app is genuinely listening for an update or something, but as we all know, a backdoor such as this can be exploited by any hackers and used in unintended ways.
By way of this post, its my sincere request to Xiaomi to fix these loopholes in their next updates. Updates should be checked by apps at certain frequency (like once in two days), not by constantly leeching in on the network resources. I really hope that some OTA update comes up soon that takes care of this.

Isn’t that just MIUI ? It has tons of cloud based features.
LikeLike
@Hanzo, When a constantly running background app randomly phones to a home server, I’m not very inclined to call that thing a “feature”. What exact feature are you talking about that needs this kind of thing?
LikeLike
Please don’t spread irresponsible FUD like this. This is most likely a connection for push messages, much like GCM on a phone running Google Apps (which incidentally also used to work over XMPP). It’s absolutely ridiculous to claim that this is a “backdoor” without any proof of malicious intent or behavior.
LikeLike
@asdfgh I forgot to mention that I’ve absolutely disabled the updates in MIUI updater. What kind of push messages am I expecting to get (I’ve greenified all messaging apps such as WhatsApp)?
As for the proof, you are right. I’d have given them the benefit of doubt, had they open sourced the Linux kernel source for MiPad. But unfortunately, they haven’t yet:
https://github.com/MiCode/Xiaomi_Kernel_OpenSource/issues/18
Since the kernel is closed-source, its up to them to prove that its not a backdoor!
LikeLike
Could be pushing anything mi-related, it could be still pushing update notifications even though you have them disabled and the updater just ignores them. regardless the connection is coming from the “Service Framework” application and not the kernel itself, having the source wouldn’t accomplish much outside of what you could do already mitm’ing it and dumping traffic.
LikeLike
Well, that’s my exact point. If I have disabled the updates, then what business does the app have to check for updates or even make network connections.
isn’t this pretty much like Microsoft telemetry thing that just can’t be disabled on the system?
LikeLike
Thank you very much for this article. Had it been an American company “phoning home” for mysterious reasons the internet would be up in arms. It seems plenty of people are willing to sell out their privacy to save a few bucks on Chinese hardware.
LikeLiked by 1 person
Its not about them being American or Chinese. Crapware is crapware, wherever it comes from. I don’t want my machines to send “tracking” or any kind of information anywhere, unless I say so.
I’m equally against the Telemetry tracking in windows-10 too. On smart-phone, you can at least root your device and disable the tracking, on windows-10 you can’t do anything!
LikeLike
Thanks, is there a full blocklist available which I can add to block all these possible ‘unwanted’ connections?
LikeLiked by 1 person
@Remco I am not aware of any entire blacklist for miui. These trackers are what I came across during my testing.
LikeLike
Thanks for your response.
But do you have a list of the domains/IP adresses you found to be tracker/backdoor related?
I would like to block them locally.
LikeLike
The only IP I found tracker related was this 111.206.200.2. You can either block this IP or the enire range if you don’t usually open Chinese websites. You can also block the domain tracker.xiaomi.com for additional security.
LikeLike
Thanks, I have blocked both domain and IP.
LikeLike
What i have done so far to temporarily fix this problem is rooted my phone (Redmi Mi4s) and removed all the MI crapware including the last service ‘Xiaomi service framework’. I have also removed all Gapps.
Now I see only the connections from the apps I launch by myself.
LikeLike